Proactively Identify and Mitigate Security Risks in Third-Party Libraries
Cyber threats are evolving, and organizations must stay ahead by securing their software supply chains. One of the biggest challenges in modern development is managing outdated and vulnerable third-party libraries, which can silently introduce security risks. Without proper visibility and monitoring, these risks can escalate into compliance violations, data breaches, and system compromises.
At Pratham Software (PSI), we recognize the importance of secure software development. That’s why we have developed an Enterprise-Grade SBOM & Vulnerability Scanner, a powerful asset designed to help you identify and mitigate security vulnerabilities in your software dependencies.
Why You Need SBOM + Trivy for Secure Development
The Growing Risk of Third-Party Libraries
As software projects evolve, incremental development often leads to obsolete dependencies. Many organizations unknowingly continue using outdated open-source libraries that may have been deprecated or have known vulnerabilities. These security flaws can be exploited by attackers, exposing your applications and data to potential threats.
A Software Bill of Materials (SBOM) helps address this challenge by providing complete transparency into all components used in your software. Trivy, an advanced vulnerability scanner, further enhances security by detecting vulnerabilities in open-source dependencies, container images, and infrastructure-as-code (IaC) configurations in real time. By combining SBOM with Trivy, organizations can proactively mitigate risks, ensuring compliance and secure software development.
Key Features of Our SBOM & Vulnerability Scanner
Comprehensive tools to secure your software supply chain and stay ahead of cyber threats.

Automated SBOM Generation
Gain complete visibility into your software components.

Real-Time Vulnerability Scanning
Detect security flaws using the latest CVE database.

Risk Classification & Prioritization
Focus on fixing the most critical vulnerabilities first.

Proactive Security Mitigation
Address security risks before they impact production.

Simplified Compliance
Generate audit-ready reports effortlessly.

Seamless Integration
Works across various development environments.
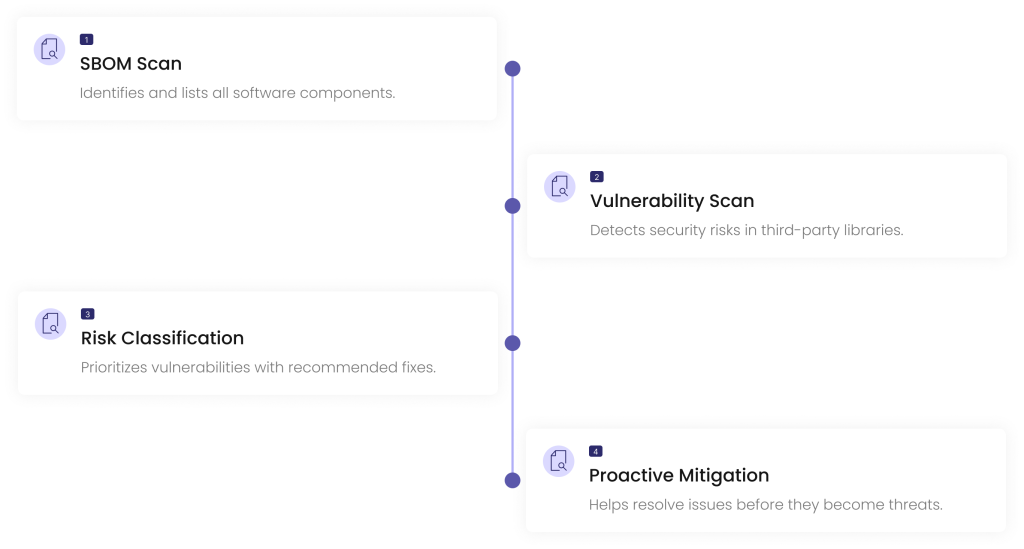
How It Works
Our streamlined process helps you detect and mitigate vulnerabilities efficiently.
What We Achieved

Automated Dependency Tracking
Ensuring transparency in software components.

Faster Risk Detection
Real-time identification of vulnerabilities.

Improved Compliance
Enhanced governance with structured reports.

Effortless Security Audits
Simplifying regulatory and security assessments..
The Business Impact: Why This Matters

Minimize Security Risks
Reduce the attack surface and avoid security breaches.

Enhance Compliance
Meet industry regulations and security standards effortlessly.

Boost Developer Productivity
Reduce manual security checks and focus on innovation.

Build Customer Trust
Secure software fosters confidence among users and stakeholders.
Get Started Today!
Take control of your software security with PSI’s Enterprise-Grade SBOM & Vulnerability Scanner. Ensure a secure, transparent, and resilient software supply chain with automated detection and proactive risk mitigation.
Written By: Punit Singhal